Blog
Our latest news.
Stay up-to-date with news and blog posts from ASMGi on how to bridge the gap to apply technology to solve business problems.
ASMGi Posts

IT Chaos Solved: Intune + Autopilot in Action

Fail SOC 2 Once – Pay Forever

Essential AI Strategies to Strengthen Third Party Risk Management

Cyber Insurance: Making the Most of Your Policy

Preventing Breaches: The Power of Security Awareness Training

Webinar: Resiliency in the Face of Ransomware

Zero Trust: A Paradigm Shift in Cybersecurity

Unveiling Deception: How to Spot Scams Before They Spot You

Ransomware: Strategies for Safeguarding Your Digital Assets

Unraveling the Power of AI in Cybersecurity: Safeguarding the Digital Realm

Fortifying Cybersecurity Defenses

Optimizing Healthcare Cybersecurity Cost and Staffing: Balancing Resources and Risk in Healthcare

Leading Cybersecurity Companies GS Lab | GAVS and ASMGi Announce Strategic Partnership to Enhance Global Cyber Defense

Understanding the Importance of Third-Party Risk Management in Healthcare

Embracing Smart Manufacturing: Unveiling IoT Trends, Challenges, and Cybersecurity in the Era of Industry 4.0
Cybersecurity Update – Terin D. Williams – DHS – CISA

Real Life Cyber Attacks - Dec 1 Event

The age of IoT and AI is quickly advancing, demanding more compute power and lower latency at the edge to ensure quick response and great performance.

xIoT Device Risk: Turning the Industry Inside-Out

Cyber Insurance: Digital Risk Mitigation Plan From Financial Loss

AI In Healthcare
Cybersecurity News from Around the Web
🕵️ Webinar: Discover and Control Shadow AI Agents in Your Enterprise Before Hackers Do
Do you know how many AI agents are running inside your business right now? If the answer is “not sure,” you’re not alone—and that’s exactly the concern. Across industries, AI agents are being set up every day. Sometimes by IT, but often by business units moving fast...
From Impact to Action: Turning BIA Insights Into Resilient Recovery
Modern businesses face a rapidly evolving and expanding threat landscape, but what does this mean for your business? It means a growing number of risks, along with an increase in their frequency, variety, complexity, severity, and potential business impact. The real...
Macs May Not Be Safe from Modern Malware
If you want extra protection, this antivirus has a lifetime subscription available for $59.99 (reg. $387).
North Korea Uses GitHub in Diplomat Cyber Attacks as IT Worker Scheme Hits 320+ Firms
North Korean threat actors have been attributed to a coordinated cyber espionage campaign targeting diplomatic missions in their southern counterpart between March and July 2025. The activity manifested in the form of at least 19 spear-phishing emails that...
DOJ Charges 22-Year-Old for Running RapperBot Botnet Behind 370,000 DDoS Attacks
A 22-year-old man from the U.S. state of Oregon has been charged with allegedly developing and overseeing a distributed denial-of-service (DDoS)-for-hire botnet called RapperBot. Ethan Foltz of Eugene, Oregon, has been identified as the administrator of the service,...
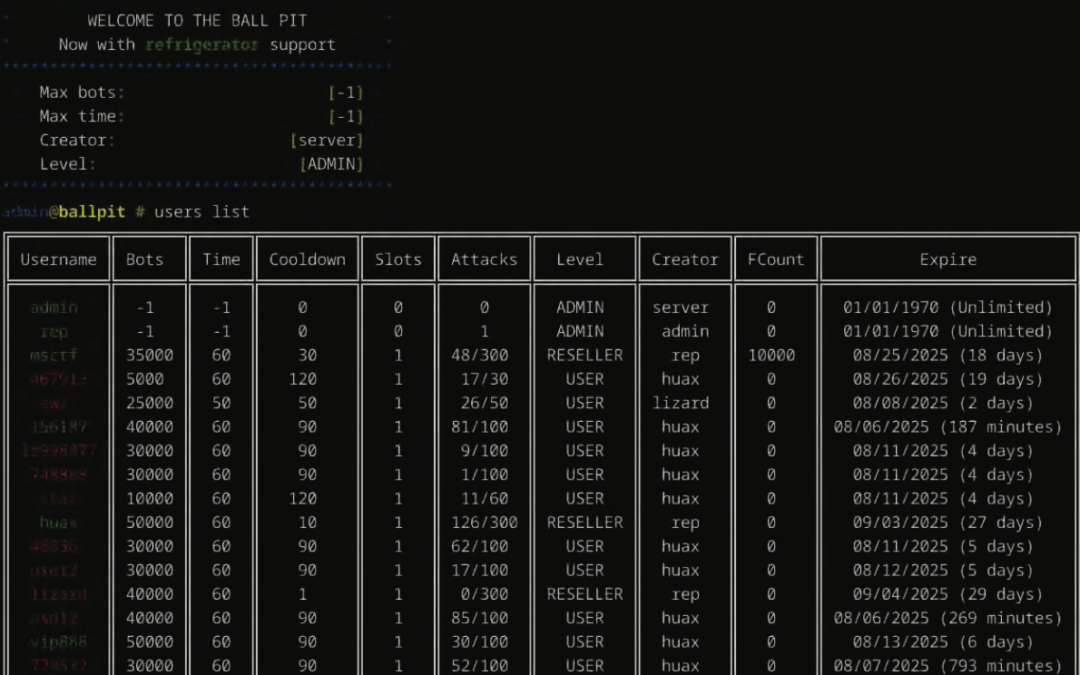
Oregon Man Charged in ‘Rapper Bot’ DDoS Service
A 22-year-old Oregon man has been arrested on suspicion of operating “Rapper Bot,” a massive botnet used to power a service for launching distributed denial-of-service (DDoS) attacks against targets — including a March 2025 DDoS that knocked Twitter/X offline. The...
Apache ActiveMQ Flaw Exploited to Deploy DripDropper Malware on Cloud Linux Systems
Threat actors are exploiting a nearly two-year-old security flaw in Apache ActiveMQ to gain persistent access to cloud Linux systems and deploy malware called DripDropper. But in an unusual twist, the unknown attackers have been observed patching the exploited...
UK Has Dropped Apple Backdoor Request, US Spy Chief Says
US Director of National Intelligence Tulsi Gabbard confirmed the news.
Workday Hit by Social Engineering Attack, Third-Party Data Exposed
Workday’s recent data breach might be tied to ShinyHunters, a group accused of exploiting Salesforce CRM at firms like Google, Adidas, Qantas, and Louis Vuitton.
New GodRAT Trojan Targets Trading Firms Using Steganography and Gh0st RAT Code
Financial institutions like trading and brokerage firms are the target of a new campaign that delivers a previously unreported remote access trojan called GodRAT. The malicious activity involves the "distribution of malicious .SCR (screen saver) files disguised as...
