Blog
Our latest news.
Stay up-to-date with news and blog posts from ASMGi on how to bridge the gap to apply technology to solve business problems.
ASMGi Posts

IT Chaos Solved: Intune + Autopilot in Action

Fail SOC 2 Once – Pay Forever

Essential AI Strategies to Strengthen Third Party Risk Management

Cyber Insurance: Making the Most of Your Policy

Preventing Breaches: The Power of Security Awareness Training

Webinar: Resiliency in the Face of Ransomware

Zero Trust: A Paradigm Shift in Cybersecurity

Unveiling Deception: How to Spot Scams Before They Spot You

Ransomware: Strategies for Safeguarding Your Digital Assets

Unraveling the Power of AI in Cybersecurity: Safeguarding the Digital Realm

Fortifying Cybersecurity Defenses

Optimizing Healthcare Cybersecurity Cost and Staffing: Balancing Resources and Risk in Healthcare

Leading Cybersecurity Companies GS Lab | GAVS and ASMGi Announce Strategic Partnership to Enhance Global Cyber Defense

Understanding the Importance of Third-Party Risk Management in Healthcare

Embracing Smart Manufacturing: Unveiling IoT Trends, Challenges, and Cybersecurity in the Era of Industry 4.0
Cybersecurity Update – Terin D. Williams – DHS – CISA

Real Life Cyber Attacks - Dec 1 Event

The age of IoT and AI is quickly advancing, demanding more compute power and lower latency at the edge to ensure quick response and great performance.

xIoT Device Risk: Turning the Industry Inside-Out

Cyber Insurance: Digital Risk Mitigation Plan From Financial Loss

AI In Healthcare
Cybersecurity News from Around the Web
Bitfinex Hack Convict Ilya Lichtenstein Released Early Under U.S. First Step Act
Ilya Lichtenstein, who was sentenced to prison last year for money laundering charges in connection with his role in the massive hack of cryptocurrency exchange Bitfinex in 2016, said he has been released early. In a post shared on X last week, the 38-year-old...
New VVS Stealer Malware Targets Discord Accounts via Obfuscated Python Code
Cybersecurity researchers have disclosed details of a new Python-based information stealer called VVS Stealer (also styled as VVS $tealer) that's capable of harvesting Discord credentials and tokens. The stealer is said to have been on sale on Telegram as far back as...
Hacker Claims 200GB Data Theft From European Space Agency — Here’s What We Know
The European Space Agency confirmed a cyber incident after a hacker claimed to access and steal data from external collaboration servers. The post Hacker Claims 200GB Data Theft From European Space Agency — Here’s What We Know appeared first on TechRepublic.
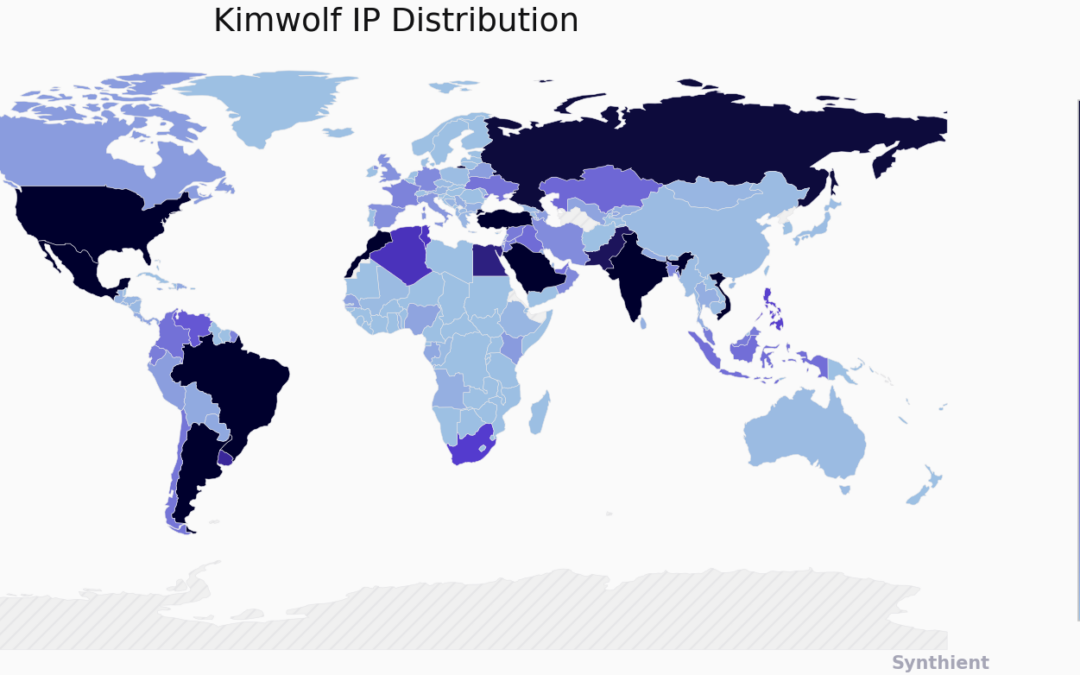
The Kimwolf Botnet is Stalking Your Local Network
The story you are reading is a series of scoops nestled inside a far more urgent Internet-wide security advisory. The vulnerability at issue has been exploited for months already, and it’s time for a broader awareness of the threat. The short version is that...
Transparent Tribe Launches New RAT Attacks Against Indian Government and Academia
The threat actor known as Transparent Tribe has been attributed to a fresh set of attacks targeting Indian governmental, academic, and strategic entities with a remote access trojan (RAT) that grants them persistent control over compromised hosts. "The campaign...
The ROI Problem in Attack Surface Management
Attack Surface Management (ASM) tools promise reduced risk. What they usually deliver is more information. Security teams deploy ASM, asset inventories grow, alerts start flowing, and dashboards fill up. There is visible activity and measurable output. But when...
Cybercriminals Abuse Google Cloud Email Feature in Multi-Stage Phishing Campaign
Cybersecurity researchers have disclosed details of a phishing campaign that involves the attackers impersonating legitimate Google-generated messages by abusing Google Cloud's Application Integration service to distribute emails. The activity, Check Point said, takes...
ThreatsDay Bulletin: GhostAd Drain, macOS Attacks, Proxy Botnets, Cloud Exploits, and 12+ Stories
The first ThreatsDay Bulletin of 2026 lands on a day that already feels symbolic — new year, new breaches, new tricks. If the past twelve months taught defenders anything, it’s that threat actors don’t pause for holidays or resolutions. They just evolve faster. This...
RondoDox Botnet Exploits Critical React2Shell Flaw to Hijack IoT Devices and Web Servers
Cybersecurity researchers have disclosed details of a persistent nine-month-long campaign that has targeted Internet of Things (IoT) devices and web applications to enroll them into a botnet known as RondoDox. As of December 2025, the activity has been observed...
How To Browse Faster and Get More Done Using Adapt Browser
As web browsers evolve into all-purpose platforms, performance and productivity often suffer. Feature overload, excessive background processes, and fragmented workflows can slow down browsing sessions and introduce unnecessary friction, especially for users who rely...
