Blog
Our latest news.
Stay up-to-date with news and blog posts from ASMGi on how to bridge the gap to apply technology to solve business problems.
ASMGi Posts

IT Chaos Solved: Intune + Autopilot in Action

Fail SOC 2 Once – Pay Forever

Essential AI Strategies to Strengthen Third Party Risk Management

Cyber Insurance: Making the Most of Your Policy

Preventing Breaches: The Power of Security Awareness Training

Webinar: Resiliency in the Face of Ransomware

Zero Trust: A Paradigm Shift in Cybersecurity

Unveiling Deception: How to Spot Scams Before They Spot You

Ransomware: Strategies for Safeguarding Your Digital Assets

Unraveling the Power of AI in Cybersecurity: Safeguarding the Digital Realm

Fortifying Cybersecurity Defenses

Optimizing Healthcare Cybersecurity Cost and Staffing: Balancing Resources and Risk in Healthcare

Leading Cybersecurity Companies GS Lab | GAVS and ASMGi Announce Strategic Partnership to Enhance Global Cyber Defense

Understanding the Importance of Third-Party Risk Management in Healthcare

Embracing Smart Manufacturing: Unveiling IoT Trends, Challenges, and Cybersecurity in the Era of Industry 4.0
Cybersecurity Update – Terin D. Williams – DHS – CISA

Real Life Cyber Attacks - Dec 1 Event

The age of IoT and AI is quickly advancing, demanding more compute power and lower latency at the edge to ensure quick response and great performance.

xIoT Device Risk: Turning the Industry Inside-Out

Cyber Insurance: Digital Risk Mitigation Plan From Financial Loss

AI In Healthcare
Cybersecurity News from Around the Web
LockBit, Qilin, and DragonForce Join Forces to Dominate the Ransomware Ecosystem
Three prominent ransomware groups DragonForce, LockBit, and Qilin have announced a new strategic ransomware alliance, once underscoring continued shifts in the cyber threat landscape. The coalition is seen as an attempt on the part of the financially motivated threat...
Step Into the Password Graveyard… If You Dare (and Join the Live Session)
Every year, weak passwords lead to millions in losses — and many of those breaches could have been stopped. Attackers don’t need advanced tools; they just need one careless login. For IT teams, that means endless resets, compliance struggles, and sleepless nights...
Severe Figma MCP Vulnerability Lets Hackers Execute Code Remotely — Patch Now
Cybersecurity researchers have disclosed details of a now-patched vulnerability in the popular figma-developer-mcp Model Context Protocol (MCP) server that could allow attackers to achieve code execution. The vulnerability, tracked as CVE-2025-53967 (CVSS score: 7.5),...
OpenAI Disrupts Russian, North Korean, and Chinese Hackers Misusing ChatGPT for Cyberattacks
OpenAI on Tuesday said it disrupted three activity clusters for misusing its ChatGPT artificial intelligence (AI) tool to facilitate malware development. This includes a Russian‑language threat actor, who is said to have used the chatbot to help develop and refine a...
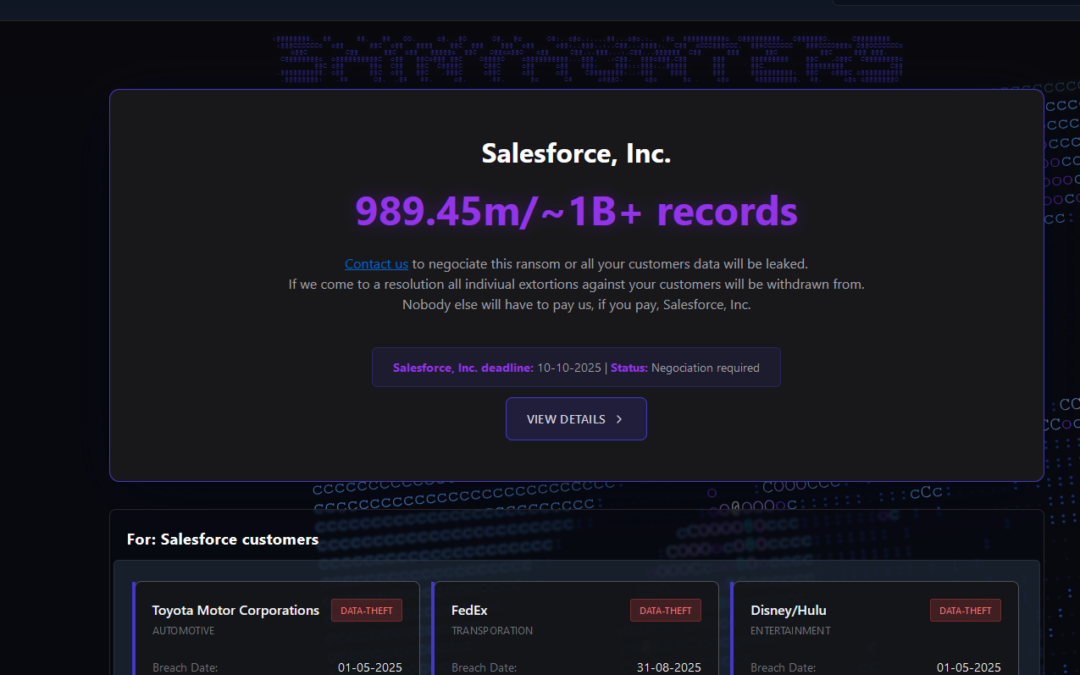
ShinyHunters Wage Broad Corporate Extortion Spree
A cybercriminal group that used voice phishing attacks to siphon more than a billion records from Salesforce customers earlier this year has launched a website that threatens to publish data stolen from dozens of Fortune 500 firms if they refuse to pay a ransom. The...
BatShadow Group Uses New Go-Based ‘Vampire Bot’ Malware to Hunt Job Seekers
A Vietnamese threat actor named BatShadow has been attributed to a new campaign that leverages social engineering tactics to deceive job seekers and digital marketing professionals to deliver a previously undocumented malware called Vampire Bot. "The attackers pose as...
Google’s New AI Doesn’t Just Find Vulnerabilities — It Rewrites Code to Patch Them
Google's DeepMind division on Monday announced an artificial intelligence (AI)-powered agent called CodeMender that automatically detects, patches, and rewrites vulnerable code to prevent future exploits. The efforts add to the company's ongoing efforts to improve...
New Research: AI Is Already the #1 Data Exfiltration Channel in the Enterprise
For years, security leaders have treated artificial intelligence as an “emerging” technology, something to keep an eye on but not yet mission-critical. A new Enterprise AI and SaaS Data Security Report by AI & Browser Security company LayerX proves just how...
XWorm 6.0 Returns with 35+ Plugins and Enhanced Data Theft Capabilities
Cybersecurity researchers have charted the evolution of XWorm malware, turning it into a versatile tool for supporting a wide range of malicious actions on compromised hosts. "XWorm's modular design is built around a core client and an array of specialized components...
13-Year-Old Redis Flaw Exposed: CVSS 10.0 Vulnerability Lets Attackers Run Code Remotely
Redis has disclosed details of a maximum-severity security flaw in its in-memory database software that could result in remote code execution under certain circumstances. The vulnerability, tracked as CVE-2025-49844 (aka RediShell), has been assigned a CVSS score of...
