by Beck Bailey | Jun 1, 2023 | RSS
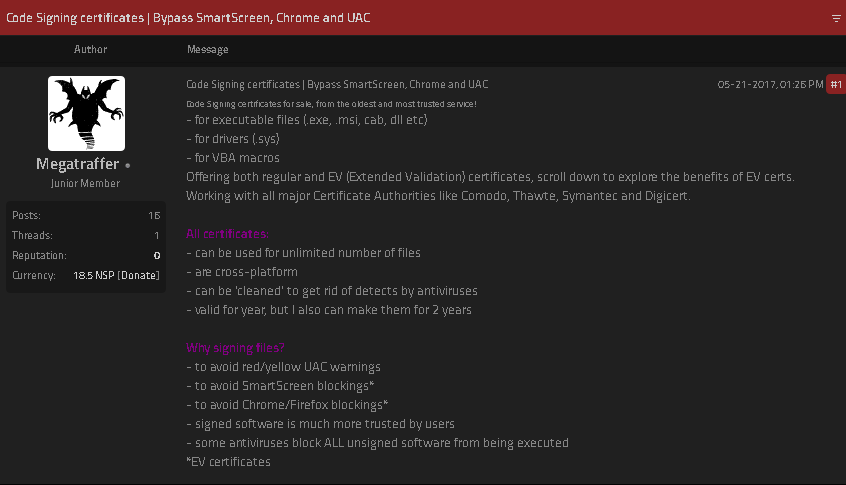
Code-signing certificates are supposed to help authenticate the identity of software publishers, and provide cryptographic assurance that a signed piece of software has not been altered or tampered with. Both of these qualities make stolen or ill-gotten code-signing...
by Beck Bailey | Jun 1, 2023 | RSS
An analysis of the “evasive and tenacious” malware known as QBot has revealed that 25% of its command-and-control (C2) servers are merely active for a single day. What’s more, 50% of the servers don’t remain active for more than a week,...
by Beck Bailey | Jun 1, 2023 | RSS
Users should be aware of what personal data is being collected and stored by Microsoft Edge and be prepared to perform periodic maintenance on that data to keep it secure. The post How to determine exactly what personal information Microsoft Edge knows about you...
by Beck Bailey | Jun 1, 2023 | RSS
Cybersecurity demands and the stakes of failing to properly secure systems and networks are high. While every organization’s specific security needs form a unique and complex blend of interconnected requirements, numerous security fundamentals almost always apply to...
by Beck Bailey | Jun 1, 2023 | RSS
A previously unknown advanced persistent threat (APT) is targeting iOS devices as part of a sophisticated and long-running mobile campaign dubbed Operation Triangulation that began in 2019. “The targets are infected using zero-click exploits via the iMessage...



Recent Comments