by Beck Bailey | Nov 21, 2025 | RSS
Ever wonder how some IT teams keep corporate data safe without slowing down employees? Of course you have. Mobile devices are essential for modern work—but with mobility comes risk. IT admins, like you, juggle protecting sensitive data while keeping teams productive....
by Beck Bailey | Nov 21, 2025 | RSS
A China-nexus threat actor known as APT24 has been observed using a previously undocumented malware dubbed BADAUDIO to establish persistent remote access to compromised networks as part of a nearly three-year campaign. “While earlier operations relied on broad...
by Beck Bailey | Nov 21, 2025 | RSS
The U.S. Securities and Exchange Commission (SEC) has abandoned its lawsuit against SolarWinds and its chief information security officer, alleging that the company had misled investors about the security practices that led to the 2020 supply chain attack. In a joint...
by Beck Bailey | Nov 21, 2025 | RSS
Salesforce has warned of detected “unusual activity” related to Gainsight-published applications connected to the platform. “Our investigation indicates this activity may have enabled unauthorized access to certain customers’ Salesforce data through...
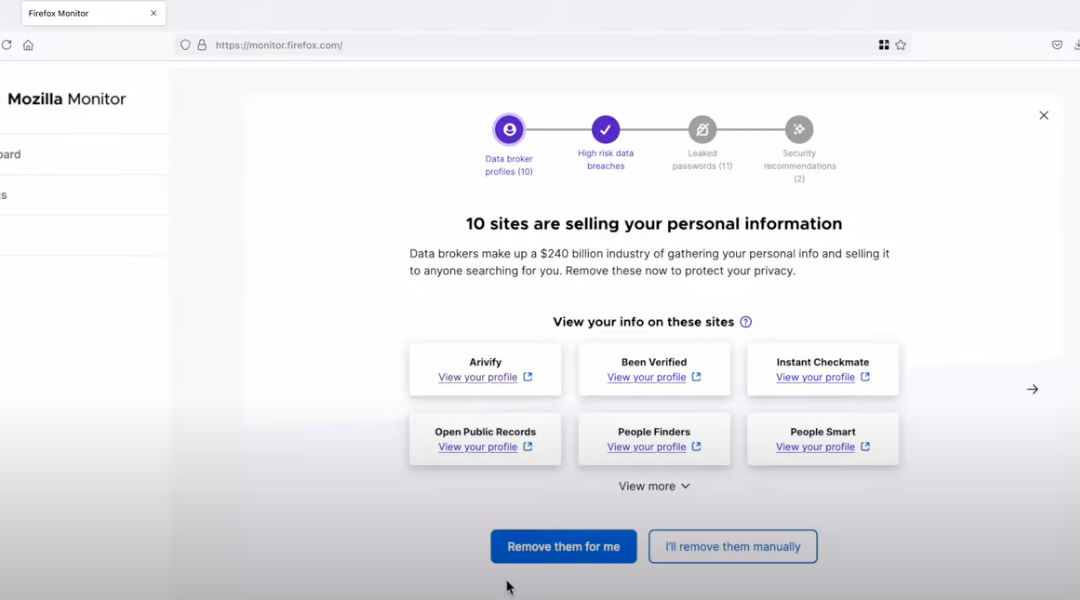
by Beck Bailey | Nov 20, 2025 | RSS
In March 2024, Mozilla said it was winding down its collaboration with Onerep — an identity protection service offered with the Firefox web browser that promises to remove users from hundreds of people-search sites — after KrebsOnSecurity revealed Onerep’s founder had...

Recent Comments